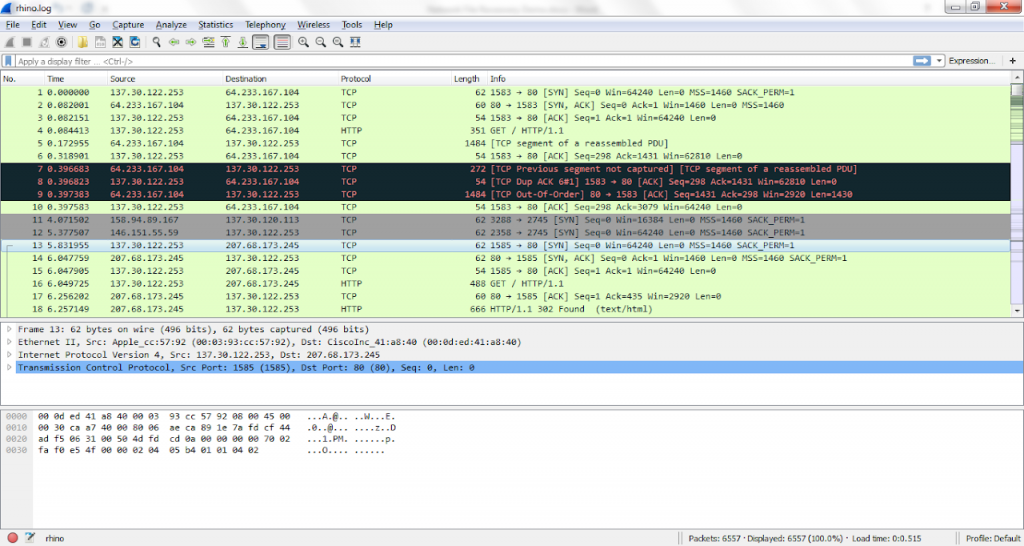
You are chatting with your friends and transferred pictures by using a popular application (which uses ftp and http, a faked scenario). However, someone intercept your traffic by sniffing the communication signals and dumped into a few log files
File Download and Detail:
- Lab Instruction
- Quiz
- Related Files
https://drive.google.com/file/d/1g36mJ3P3nDhpdtB10tJVCHNa8o_4eRYH/view?usp=sharing
https://drive.google.com/file/d/1F57YqmF1Ti60MEci1W97ylo3xn6t94oQ/view?usp=sharing